32:06

Information Theory and Neural Coding - Part 1, by Adam Schneider
Information theory, developed by Claude Shannon in 1949, provides mathematically rigorous ...
published: 08 Jul 2013
author: CAMBAM Students
Information Theory and Neural Coding - Part 1, by Adam Schneider
Information Theory and Neural Coding - Part 1, by Adam Schneider
Information theory, developed by Claude Shannon in 1949, provides mathematically rigorous tools to quantify the precision with which a systems output contain...- published: 08 Jul 2013
- views: 31
- author: CAMBAM Students
69:21

CESG Fishbowl Seminar: Shannon Information Theory and Sparse Recovery
Abstract: The problem of sparse recovery arises in a number of statistical signal processi...
published: 18 Feb 2013
author: CESG TAMU
CESG Fishbowl Seminar: Shannon Information Theory and Sparse Recovery
CESG Fishbowl Seminar: Shannon Information Theory and Sparse Recovery
Abstract: The problem of sparse recovery arises in a number of statistical signal processing and learning applications. Sparsity arises from the fact that th...- published: 18 Feb 2013
- views: 107
- author: CESG TAMU
56:01

Information Theory Today: ECE Lecturer Series
Founded by Claude Shannon in 1948, information theory has taken on renewed vibrancy with t...
published: 11 Sep 2012
author: UnivDelaware
Information Theory Today: ECE Lecturer Series
Information Theory Today: ECE Lecturer Series
Founded by Claude Shannon in 1948, information theory has taken on renewed vibrancy with technological advances that pave the way for attaining the fundament...- published: 11 Sep 2012
- views: 1545
- author: UnivDelaware
3:36

Safe and Secure Communications:Ohtsuki Group,Keio University
In recent years, wireless communication has become very familiar, as exemplified by the ra...
published: 05 Jan 2010
author: keiouniversity
Safe and Secure Communications:Ohtsuki Group,Keio University
Safe and Secure Communications:Ohtsuki Group,Keio University
In recent years, wireless communication has become very familiar, as exemplified by the rapid spread of mobile phones. However, because the available frequen...- published: 05 Jan 2010
- views: 1659
- author: keiouniversity
134:10
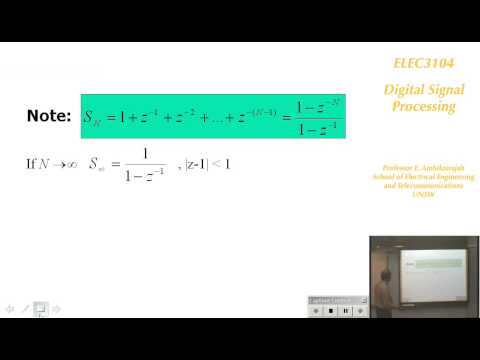
Digital Signal Processing 3: Introduction to Z-Transorm - Prof E. Ambikairajah
Digital Signal Processing Introduction to Z-Transorm Electronic Whiteboard-Based Lecture....
published: 24 Mar 2009
author: UNSWelearning
Digital Signal Processing 3: Introduction to Z-Transorm - Prof E. Ambikairajah
Digital Signal Processing 3: Introduction to Z-Transorm - Prof E. Ambikairajah
Digital Signal Processing Introduction to Z-Transorm Electronic Whiteboard-Based Lecture.- published: 24 Mar 2009
- views: 15359
- author: UNSWelearning
51:01

Lec 5 | MIT RES.6-008 Digital Signal Processing, 1975
Lecture 5: The z-transform Instructor: Alan V. Oppenheim View the complete course: http://...
published: 07 Dec 2011
author: MIT
Lec 5 | MIT RES.6-008 Digital Signal Processing, 1975
Lec 5 | MIT RES.6-008 Digital Signal Processing, 1975
Lecture 5: The z-transform Instructor: Alan V. Oppenheim View the complete course: http://ocw.mit.edu/RES6-008S11 License: Creative Commons BY-NC-SA More inf...- published: 07 Dec 2011
- views: 7815
- author: MIT
2:31

CTTC coorganizes the ISWCS'2014
The aim of this symposium is to provide a forum for researchers and technologists to prese...
published: 13 Nov 2013
CTTC coorganizes the ISWCS'2014
CTTC coorganizes the ISWCS'2014
The aim of this symposium is to provide a forum for researchers and technologists to present new ideas and contributions in the form of technical papers, panel discussions as well as real-world evaluation of many ideas in wireless communications, networking and signal processing employed to support the needs of the Information Society. This eleventh symposium will bring together various wireless communication systems developers to discuss the current status, technical challenges, standards, fundamental issues, and future services and applications. ISWCS'14 seeks to address and capture highly-innovative and state-of-the-art research from academia, the wireless industry as well as standardization advances. The scope of the conference includes a wide range of technical challenges encompassing wireless communications, information theory, quality of service support, networking, signal processing, cross-layer design for improved performance, and future wireless broadband systems. - See more at: http://www.cttc.es/2013/10/24/cttc-coorganizes-the-iswcs2014/#sthash.jmRIr40a.dpuf- published: 13 Nov 2013
- views: 1
1:29

2013 SA Pearcey Enterpreneur - Dr Alex Grant
Alex Grant is the Director of the Institute for Telecommunications Research at the Univers...
published: 20 Jun 2013
author: iAwards
2013 SA Pearcey Enterpreneur - Dr Alex Grant
2013 SA Pearcey Enterpreneur - Dr Alex Grant
Alex Grant is the Director of the Institute for Telecommunications Research at the University of South Australia. He has lead the Coding and Information Theo...- published: 20 Jun 2013
- views: 30
- author: iAwards
9:10

Information bottleneck-based relevant knowledge representation
A novel representation technique for sparse information, based on information theory.Throu...
published: 04 Nov 2013
Information bottleneck-based relevant knowledge representation
Information bottleneck-based relevant knowledge representation
A novel representation technique for sparse information, based on information theory.Through Information Bottleneck paradigm the optimal data representation in the SOM-space has been determined as a trade-off between the signal reconstruction capabilities and the original data statistical similarities preservation.- published: 04 Nov 2013
- views: 25
54:34

Lecture - 9 Information Theory (Part - 2)
Lecture Series on Digital Communication by Prof.Bikash. Kumar. Dey , Department of Electri...
published: 28 Aug 2008
author: nptelhrd
Lecture - 9 Information Theory (Part - 2)
Lecture - 9 Information Theory (Part - 2)
Lecture Series on Digital Communication by Prof.Bikash. Kumar. Dey , Department of Electrical Engineering,IIT Bombay. For more details on NPTEL visit http://...- published: 28 Aug 2008
- views: 22146
- author: nptelhrd
9:59

CERIAS Security: John Oritz: Steganography 1/6
Clip 1/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer...
published: 30 Apr 2010
author: Christiaan008
CERIAS Security: John Oritz: Steganography 1/6
CERIAS Security: John Oritz: Steganography 1/6
Clip 1/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer science whose aim is to conceal the existence of information. Steg...- published: 30 Apr 2010
- views: 873
- author: Christiaan008
22:05

Aliasing in Sampled Systems
An intuitive approach to understanding aliasing in sampled systems using a strobe-sampled ...
published: 02 Jun 2013
author: ejacobsen1
Aliasing in Sampled Systems
Aliasing in Sampled Systems
An intuitive approach to understanding aliasing in sampled systems using a strobe-sampled helicopter rotor as a demonstration. For more information visit htt...- published: 02 Jun 2013
- views: 46
- author: ejacobsen1
57:55

2008-11-12 CERIAS - John Oritz, SRA International
Recorded: 11/12/2008 CERIAS Security Seminar at Purdue University John Oritz, SRA Internat...
published: 10 May 2012
author: ceriaspurdue
2008-11-12 CERIAS - John Oritz, SRA International
2008-11-12 CERIAS - John Oritz, SRA International
Recorded: 11/12/2008 CERIAS Security Seminar at Purdue University John Oritz, SRA International John Oritz, SRA International Steganography is a discipline o...- published: 10 May 2012
- views: 69
- author: ceriaspurdue
84:17

Social Signal Processing Summer School - Claes Strannegård - What is it like to be a bee?
Claes Strannegård is an associate professor at the Department of Philosophy, Linguistics a...
published: 12 Aug 2013
Social Signal Processing Summer School - Claes Strannegård - What is it like to be a bee?
Social Signal Processing Summer School - Claes Strannegård - What is it like to be a bee?
Claes Strannegård is an associate professor at the Department of Philosophy, Linguistics and Theory of Science, University of Gothenburg and the Department of Applied Information Technology at Chalmers University of Technology. The ability to learn, neuroplasticity, enables honey bees to adapt to new environments and perform a wide range of cognitive tasks in those environments. Honey bees outperform artificial systems both in versatility and robustness and therefore their neurophysiology could provide valuable clues to artificial general intelligence. Reward seems to play a central role in guiding the learning process of bees, both when learning which perceptual patterns are associated with reward and which actions to take when a given perceptual pattern occurs, so as to satisfice reward. I present a graph-based computational model of memory development. In this model all learning is driven by reward. The model learns (i) memory structures representing perceptual patterns of the environment and (ii) actions that manipulate the environment. The goal is to combine automatic concept development with a variation of reinforcement learning. In social animals such as bees, part of the reward signals come from the social environment. Thus the nervous system is partly shaped by social signals. Similarly, our computational model is partly shaped by feedback signals from humans that interact with it. The human user has the options of staying passive or interfering actively by encouraging or discouraging certain kinds of behavior.- published: 12 Aug 2013
- views: 30
Vimeo results:
4:05

Digging in the Crates
http://ditc.weaintplastic.com
http://www.weaintplastic.com
Digging in the crates - The di...
published: 14 Mar 2010
author: WE AIN\'T PLASTIC
Digging in the Crates
http://ditc.weaintplastic.com
http://www.weaintplastic.com
Digging in the crates - The digging in record crates to find rare pieces of music that can be used for new productions, has long been a ritual of a scene within the music culture. Since the mid-20th Century it is called sampling, when digitized sound samples of existing musical works are edited, rearranged and used in modern music productions.
An interactive installation offers possibilities to explore sampling as a production technology of contemporary music. While modified turntables are used to navigate dynamic data visualizations, information graphics as well as auditory contributions are helping to understand complex contents and relations. Besides the history of sampling or technical backgrounds of the digitization of analog audio signals, visitors can also obtain information on the dissociation of sample-based productions and other musicological phenomena such as remixes, mashups or covers. As a highlight of the exhibition the visitor can slip into the role of a producer and goes on a fascinating search for suitable samples, which will be found on soul, funk and jazz records of the 70s and 80s.
Depending on user interests, Digging in the Crates offers different approaches to the topic. The visitor acts in a totally free interaction-space, which allows him to consider sampling from completely different perspectives. The straight interaction with information is just as important as the possibility to deal with "sampling" in a passive way. This means the user can slip into an active role in which he has full control over the visualized information as well as taking a rather passive attitude to get inspired by the interactions of others.
Digging in the Crates aims to describe the sampling culture in all its aspects, characteristics, and influences. Not only the understanding of the creative process as a craft but also the effort and creative processes associated with sampling should be communicated authentically.
9:40

Jerry's Map
Artist Jerry Gretzinger reveals the process and philosophy behind his decades-long mapping...
published: 24 Jul 2010
author: gregory whitmore
Jerry's Map
Artist Jerry Gretzinger reveals the process and philosophy behind his decades-long mapping project.
Jerry Gretzinger's Map Blog:
http://jerrysmap.blogspot.com/
Radio NZ interview with Greg Whitmore
http://www.radionz.co.nz/national/programmes/nights/20110921
The Atlantic:
http://www.theatlantic.com/video/archive/2011/09/mapping-the-void/245858/
Essay: Mapping “The Void” : Tasks, Information Seeking & Flow Theory in the Phenomenology of “Jerry’s Map”
http://bombus.org/mapping_the_void_essay
Reddit:
http://www.reddit.com/r/jerrys_mod
0:50

Signal To Noise - release, LAb[au], 2012
'Signal To Noise' is a kinetic installation immersing the spectator in patterns of sonic m...
published: 15 May 2012
author: LAb[au]
Signal To Noise - release, LAb[au], 2012
'Signal To Noise' is a kinetic installation immersing the spectator in patterns of sonic motion, based on generative principles executed by 512 mechanical split-flaps. The expression ‘signal-to-noise’ is a measure used to quantify how much a signal has been lost to noise; it’s a ratio of useful to un-useful information in a data exchange. The works consists of a 3.40 m circular structure, containing 4 horizontal rows of 128 split-flaps at eye height. The external surface exposes the stripped back technology of the split-flaps and driver boards, while the internal surfaces reveal the characters of the split-flaps. The circular installation invites the visitor to plunge into a kinetic composition in the midst of the eternal calculation process of an auto-poetic machine. The split-flaps are constantly spinning on a variable speed/rhythm which is dependent upon on the underlying algorithm, analyzing in the maze of information the appearance of a word-equal-meaning.
14:48

Wrathful King Kong Core _ by Lu Yang ( music by Yao Dajuin )
In Dharma-ending times, when all living things are unruly, afflicted with hubris, kindness...
published: 28 Sep 2011
author: LuYang
Wrathful King Kong Core _ by Lu Yang ( music by Yao Dajuin )
In Dharma-ending times, when all living things are unruly, afflicted with hubris, kindness and morality fade, evil and sin prevail, and none comprehend their true nature. The wrathful deities, beholden to their duty, shall vanquish all demons, and with their merciful fire, destroy all evil beings, leaving none behind.Though their wrathful visages may terrify, they are an expression of the Buddha's infinite mercy.
When the dead look upon them, they need not fear, for they are not corporeal, and no harm can befall them.When the first signs of anger reach the human brain, the information is first transmitted to the hypothalamus.This activates the amygdalae to carry out certain processes, which in turn set off a chain reaction by activating a number of other structures in the brain.These structures are responsible for transforming nerve signals into visible expressions of anger.
This project is a foolhardy attempt to superimpose religious concepts of wrathful deities onto scientific theories of the brain's anger response mechanisms.
Youtube results:
3:19

Nyquist
just in case you dont know what this means here is a definition
he Nyquist--Shannon sampl...
published: 10 Sep 2013
Nyquist
Nyquist
just in case you dont know what this means here is a definition he Nyquist--Shannon sampling theorem, after Harry Nyquist and Claude Shannon,[1] in the literature more commonly referred to as the Nyquist sampling theorem or simply as the sampling theorem, is a fundamental result in the field of information theory, in particular telecommunications and signal processing. Sampling is the process of converting a signal (for example, a function of continuous time or space) into a numeric sequence (a function of discrete time or space). Shannon's version of the theorem states:[2] If a function x(t) contains no frequencies higher than B hertz, it is completely determined by giving its ordinates at a series of points spaced 1/(2B) seconds apart. In other words, a bandlimited function can be perfectly reconstructed from a countable sequence of samples if the bandlimit, B, is no greater than half the sampling rate (samples per second). The theorem also leads to a formula for reconstruction of the original function from its samples. When the bandlimit is too high (or there is no bandlimit), the reconstruction exhibits imperfections known as aliasing. The Poisson summation formula provides a graphic understanding of aliasing and an alternative derivation of the theorem, using the perspective of the function's Fourier transform.- published: 10 Sep 2013
- views: 18
23:31

Q1: Guest Lecture: Sundeep Rangan
Sundeep Rangan received the B.A.Sc. at the University of Waterloo, Canada and the M.Sc. an...
published: 23 Sep 2012
author: Network20Q
Q1: Guest Lecture: Sundeep Rangan
Q1: Guest Lecture: Sundeep Rangan
Sundeep Rangan received the B.A.Sc. at the University of Waterloo, Canada and the M.Sc. and Ph.D. at the University of California, Berkeley, all in Electrica...- published: 23 Sep 2012
- views: 304
- author: Network20Q
9:59

CERIAS Security: John Oritz: Steganography 5/6
Clip 5/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer...
published: 30 Apr 2010
author: Christiaan008
CERIAS Security: John Oritz: Steganography 5/6
CERIAS Security: John Oritz: Steganography 5/6
Clip 5/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer science whose aim is to conceal the existence of information. Steg...- published: 30 Apr 2010
- views: 240
- author: Christiaan008
8:04

CERIAS Security: John Oritz: Steganography 6/6
Clip 6/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer...
published: 30 Apr 2010
author: Christiaan008
CERIAS Security: John Oritz: Steganography 6/6
CERIAS Security: John Oritz: Steganography 6/6
Clip 6/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer science whose aim is to conceal the existence of information. Steg...- published: 30 Apr 2010
- views: 160
- author: Christiaan008











